 This is Part 2 of a four-part series about a chief information security officer’s initial 365 days. You can read Part 1 here. I will focus on and emphasize the importance of risk in this article.
This is Part 2 of a four-part series about a chief information security officer’s initial 365 days. You can read Part 1 here. I will focus on and emphasize the importance of risk in this article.
Quite often, cyber leaders are drowned in the complexities of technology, operational issues and corporate politics. Risk identification, assessment and management is generally missed. However, risk management is very high on the leadership team and the board’s agendas.
Second Quarter Goals – Enterprise Risk, Organizational Development, Portfolio Planning and Security Architecture
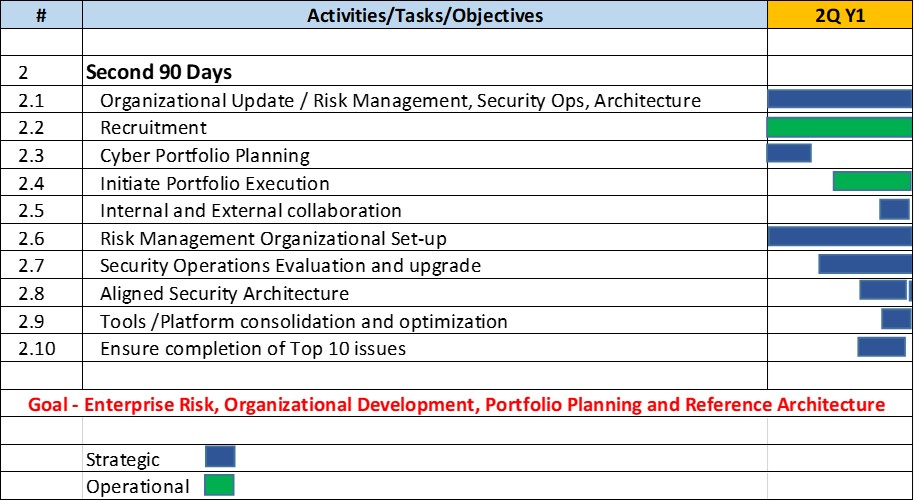
Figure 1: Second 90-Day Plan
Refer to Figure 1 for a list of planned activities that I call the “Two by Ten” series. As displayed in the figure, some of the strategic activities from the first 90 days will turn operational in the next 90 days period.
Organizational Update – Risk Management, Security Operations & Architecture
The creation of a risk management division for the cybersecurity organization as an enabler will be a major accomplishment. Quite often, organizations do not have the enterprise view of their risks and the impacts on their businesses. This, along with the categorized or quantified risks, will help with the budget and investment planning. This initiative will address the assessment gaps and enhance the cybersecurity posture.
Recruitment
Based on the first quarter’s resource evaluation and need analysis, recruitment becomes an essential element to implement the program portfolio. Key success factors include keeping the teams lean and collaborating with each other, aligned with the strategic goals, and leveraging the ecosystems.
Cyber Portfolio Planning and Execution
Planning the program portfolio to address the assessment gaps will be a critical task during this 90-day period. Portfolio execution using the organizational guidelines for the project management will follow the planning. Timely completion of the projects with planned return on investment (ROI) is critical for success.
Internal and External Collaboration
It is a proven fact that collaboration is the key to survival in the cybersecurity world. A CISO’s success depends on internal collaboration as well as leveraging external cyber forums and entities.
Risk Management Organizational Setup
As clearly identified by the assessment gaps, subsequently documented in the cyber strategy, a risk management unit set-up is strategic to leveraging the governance, risk, and compliance (GRC) platform. The rollout of this capability provides an enterprise view of the risk to assist quantifying the risk for C-suite and board. Refer to Figure 2 below for the internal risk ecosystem consisting of the Enterprise Risk Committee, Chief Risk Officer and Chief Information Security Officer. This is mostly applicable to large organizations.
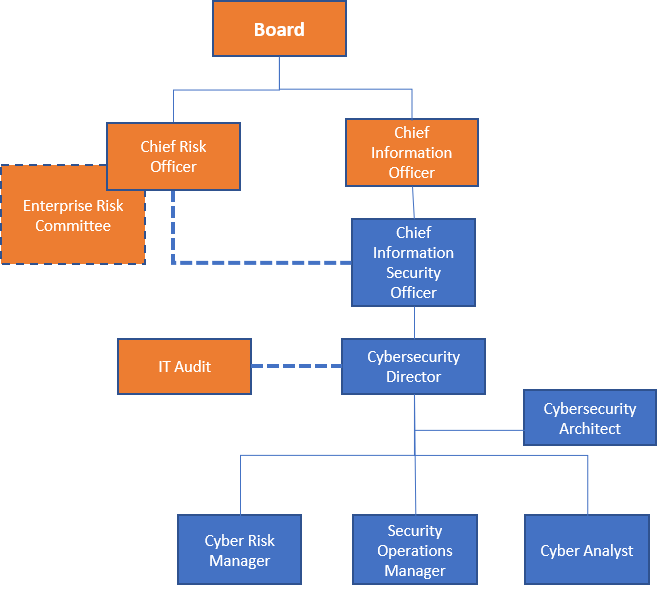
Figure 2: Risk ecoystem
Security Operations Evaluation and Upgrade
Security operations, which provide a 24/7 lookout for the network and IT assets, need to be future-proofed. The security operations need reorganization, a platform roadmap, leadership and continuous training. A security operations upgrade based on the people, process and technology aspects should be planned and the implementation initiated.
Aligned Security Architecture
Security architecture should be aligned with enterprise security and can provide internal consulting support for activities like product selection, technology roadmap and policy implementation ensuring CISO’s success.
Tools and Platform Consolidation and Optimization
This critical activity aligned with the security operations upgrade (quite often labeled as 2.0 or next-generation) is to optimize the utilization of the existing tools and platforms. Orchestration of the tools provided data exchange between the platforms and delivery of required threat intelligence to the team.
Ensure Completion of Top 10 Issues
Keeping up with the first 90 days goal of resolving the top 10 issues, the CISOs needs to keep this score moving in a positive direction. The business partners are looking for an outcome-based cybersecurity organization. All of the critical planning and execution activities in the first 180 days should result in issues being resolved, and the cybersecurity posture going up and critical risks being managed.
Key Takeaways
- Develop a trusted relationship within and outside the ecosystem. Please refer to my article on, “The Importance of Cybersecurity Ecosystem.”
- Establish the risk ecosystem with linkage to all cybersecurity components. It is all about risk.
- Ensure the evolving cybersecurity organization is outcome-based and resolving the issues in a constructive manner.
Rajiv has more than 25 years of information technology strategy, operations, large systems integration, cyber security and program management experience. Rajiv is a principal with Plante Moran management Consulting, cybersecurity practice after serving as Chief Information Security Officer (CISO) for the Department of Technology, Management and Budget, State of Michigan.




Leave a Reply
You must be logged in to post a comment.