On Monday, June 8, the White House Office of Management and Budget (OMB) released a final memorandum mandating that all Federal websites implement HTTPS (Hypertext Transfer Protocol Secure). By December of 2016, all Federal websites will need to implement HTTPS for all communications.
Why the Mandate?
Privacy, web communications, and encryption are certainly in the news. For a long time, HTTP minus the S has been the standard for most websites. Websites that manage financial transactions, personal health information, and other potentially sensitive information have utilized HTTPS, while many others have relied solely on HTTP. In recent years (in no small part due to revelations by Edward Snowden), there has been a significant shift towards encrypting all communications:
- Twitter offered optional encryption in 2011, and began enforcing encryption by default in 2012
- Facebook turned on encryption by default in June 2013
- Google began encrypting GMail by default in 2010, and made all search traffic (including anonymous searches) encrypted by default in March 2014
- In breaking news this past week at the World Wide Developer Conference (WWDC), Apple has announced that iOS9 will encourage developers to exclusively use HTTPS over HTTP.
The movement towards encrypting all communications received a shot in the arm with Google’s decision to encrypt all search traffic in 2014. In essence, Google’s announcement signaled a new standard for privacy:
- Treat all user inputs as containing potentially sensitive or personal information, whether someone is searching for the closest Toys R Us or the closest STD clinic. Encrypt this traffic.
- Treat all wifi connections as potentially vulnerable, from the open network at your local Starbucks to your mobile device to an LTE network. Encrypt this traffic.
HTTPS Treats All User Data as Sensitive
Internet communications go beyond just the information presented on the web page – each browser sends information to the web server – information like the type of browser (ex. Firefox 38.0.5 or Internet Explorer 9), the user’s operating system (ex. Windows, Android, iOS, or Linux), device (ex. Apple iPhone 6, Nokia Lumia 520, or Apple MacBook Pro), IP address, etc. There’s a lot that gets sent with each package, information that can be sorted and parsed if it is passed around in the open, unencrypted. While that information doesn’t necessarily contain personally identifiable information (PII), it could be used to create a profile of linked data that potentially identifies an individual.
This is especially relevant to Federal websites. They exist for the public, either by providing an essential service or communicating important information. The breadth of content and services provided by the more than 1300 top-level domains is comprehensive – there is a lot there. A user may seek information about the weather, official government time, a sensitive mental health condition, or what to do in an emergency.
Because there are so many potentially sensitive transactions occurring in the open, encrypting all communications via HTTPS is the only current standard in place to ensure this information is kept private, no matter the subject matter. By establishing the HTTPS everywhere standard, OMB and the Federal CIO are saying that all transactions between Federal websites and users are potentially sensitive and we should do everything possible to protect the privacy of individual users.
Encryption Matters
Encryption matters because it guarantees that people are connecting to the official place they intend to go and that browser activity is kept private. Web pages, URL’s, cookies, and headers are all encrypted. It’s secure. It’s private.
There are additional benefits to https now. Google Search algorithms now prefer encrypted websites. The White House, the UK Government Digital Service, and GSA 18F are all using encryption by default. In short – it’s becoming a standard and with this memorandum it will now be required.
HTTPS Doesn’t Impact Web Performance
The primary reasoning I have heard against encryption is website performance. The encryption/decryption steps slow down the browser and the entire experience lags. However, as operating systems and browsers have improved, so has their ability to quickly handle the secure handshake between browser and web server that verifies a safe connection.
Even more telling, Google is obsessive about web performance. They have done beta testing where they add features that slow down the web experience, in order to capture metrics regarding click-through rates, bounces, and exits. Google’s revenue is tied to their performance and they can reliably predict that a 200 millisecond delay will result in a certain amount of lost revenue.
But Google has encrypted everything now. If HTTPS was that significant of a performance impact, if it resulted in significant revenue lost, would Google implement it? Likely not. Instead, they are among many other web companies improving the performance of the HTTPS standard, through tools like SPDY (the acronym means nothing, so feel free to call it “spidey”) and contributions to the upcoming HTTP/2 (an encrypted by default) web protocol.
In sum: the big web companies have a vested interest in making the web fast and secure. The performance tradeoffs between HTTP and HTTPS have been minimized to the millisecond. There are great tools like webpagetest.org that measure all sorts of performance metrics, so if you remain skeptical about the tradeoffs – plug your site in and test.
How to Get There
Migrating from the open HTTP protocol to HTTPS takes some work, but most of the steps necessary can be accomplished by a small team over the course of a few development sprints. It may not be simple, but a systematic approach and experienced team can make the migration process relatively painless.
Already, 18f has published their helpful recommendations on HTTPS implementation, including some configuration and technical specifications. Some agencies have gone the extra mile of adding HSTS (HTTP Strict Transport Security), which forces only HTTPS traffic and hard codes that rule into browsers like Chrome and Firefox.
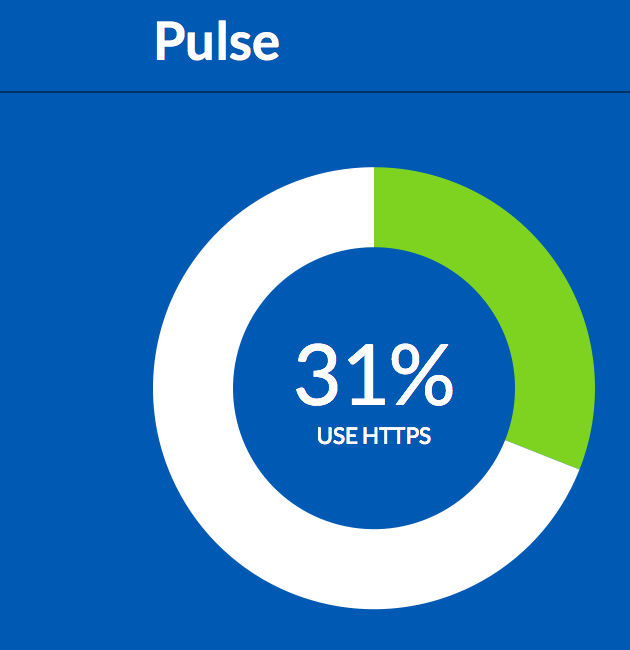
There are some helpful tools out there to test your HTTPS configuration and verify the right settings are in place. We recommend SSL Test, a tool that provides solid recommendations, a comprehensive list of server and SSL certificate specifications, and a nice grading system for HTTPS implementation. In addition, 18f has developed Pulse to track the adoption of HTTPS (as well as the Digital Analytics Program) across the top level Federal domains. As of May 29, 2015, 31% of Federal websites are using HTTPS, leaving another 69% approximately 18 months to migrate to HTTPS and meet the new OMB standard.
The clock is ticking.




Leave a Reply
You must be logged in to post a comment.