![]()
I’m going to skip the third principle of resource management for now. Risk management is the next principle. The only premise about risk management comes from Tim Lister:
Risk Management is How Adults Manage Projects
If risk management is how adults manage projects, here are some principles (sub irreducible principles) of project management.
These five principles are simple, obvious, but difficult to implement. The reason they’re difficult is that most people shy away from risk. Managing in the presence of risk does not come naturally.
It is a learned behavior. And once learned it has to be practiced. But before it can be learned and then practiced, “managing in the presence of risk,” must become part of the business culture.
Some cultures do this better than others. NASA is probably better than others. But even NASA has moved a risk adverse culture in the past decades.
- Hoping that something positive will result is not a very good strategy. Preparing for success is the basis of success.
- Single point estimates are no better than 50/50 guesses in the absence of knowledge of the standard deviation of the underlying distribution.
- Without connecting cost, schedule, and technical performance of the effort to produce the product or service the connection to value cannot be made.
- Risk management is not an ad hoc processes that you can make up as you go. A formal foundation for risk management is needed.
- Identifying risks without communication them is a waste of time.
Each of these 5 principles must be addressed by the risk management process.
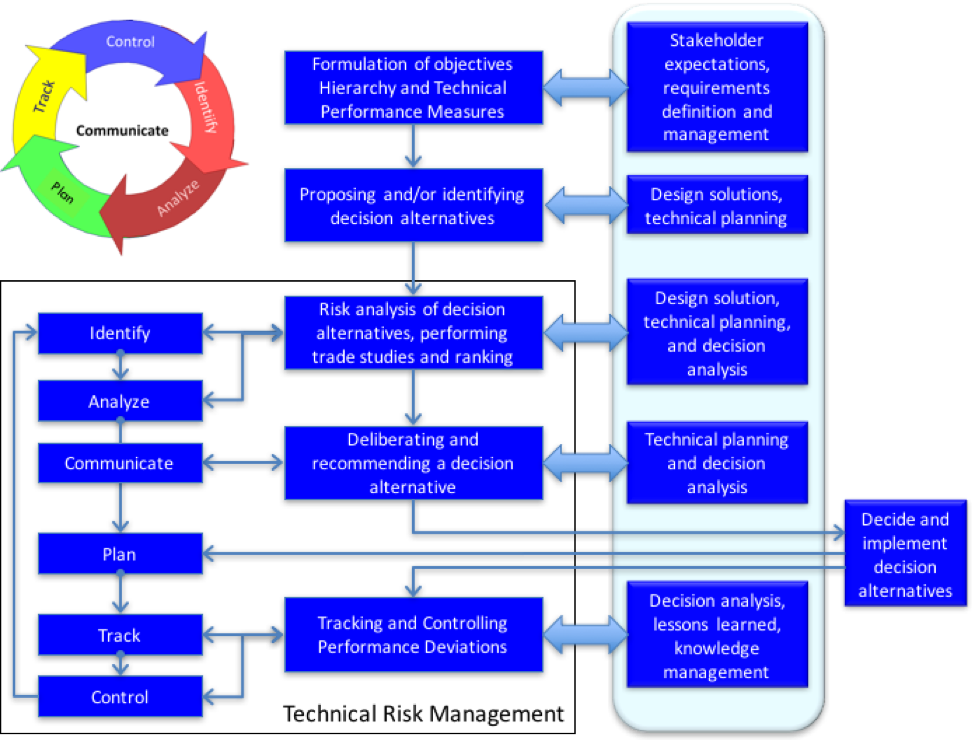
Continuous risk management is based on the underlying principles, concepts, and functions of risk management and provides guidance on how to implement it as a continuous practice in projects and organizations.
Risk management is used to continuously assess what can go wrong in projects (i.e., what the risks are), determine which of these risks are most important, and implement strategies to deal with these risks. These principles are based on proven practices confirmed through research, field testing, and direct work with clients.
Risk identification is an ongoing activity that takes place during the routine program workflow. Project activities such as programmatic and technical meetings, telecons, reviews, and other forms of communication often bring to light program risks. When this occurs, we record and analyze the risk on a Risk Information Sheet. The process outlined below helps the program team identify and cope with program risks throughout the life of the program.
- Team identifies list of potential risk items. Not all items identified are accepted. Risks can be current problems or potential future problems.
- Risk Mitigation plan with action items and due dates is developed for each accepted risk item.
- Team meets regularly (every 2 weeks for example) to assess risks and add new risk items, if necessary. See Status section on Risk Information Sheet below.
- Risks are closed when all the actions to close the risk have been taken. Some risk items are closed quickly; others are open for a long time. Some are considered watch items and the action plan doesn’t kick in until certain negative events happen.
- Action plans include second sources of some items, requirements redirection, different technologies, etc.
- Closed risks remain in the base for future learning.
Continuous risk management, when performed successfully, provides a number of benefits:
- Prevents problems before they occur – identifies potential problems and deals with them when it is easier and cheaper to do so – before they are problems
- Improves product or service quality – focuses on the program’s objectives and consciously looks for things that many affect quality throughout the program lifecycle.
- Enables better use of resources – allows the early identification of potential problems – proactive management – and provides input into management decisions regarding resource allocation.
- Promotes teamwork – involves personnel at all levels of the program.
Glen Allenman is part of the GovLoop Featured Blogger program, where we feature blog posts by government voices from all across the country (and world!). To see more Featured Blogger posts, click here.




Leave a Reply
You must be logged in to post a comment.