Having the necessary tools is step one for shifting to telework. Are organizations providing the necessary equipment, connection, access and security to employees?
For security purposes, having the right equipment is pertinent for the government workforce. Yet, while 71% of respondents said their agencies provided the necessary tools and equipment, fewer — 57% — said their agencies were able to enforce existing security measures (See Figures 8 and 9).
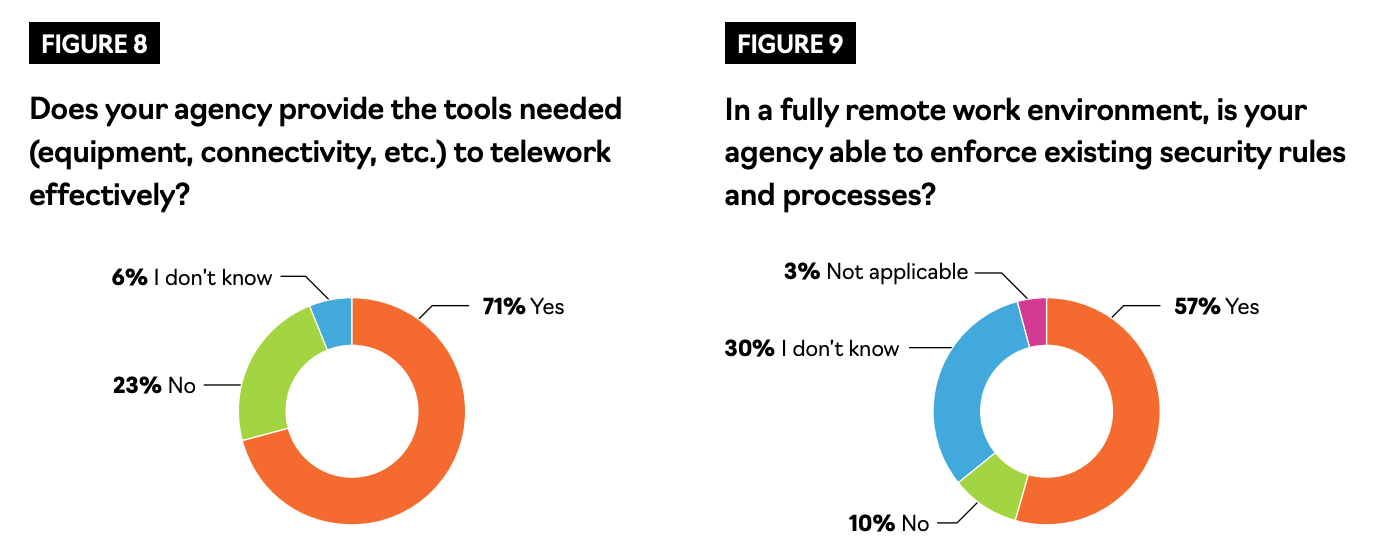
In other words, while government employees are likely to have the devices they need, they are less likely to have the security that is required.
From the beginning of the outbreak, malicious cyber actors have been feeding off of public paranoia surrounding the novel coronavirus. Add in the hundreds of thousands of employees now working from home, and the level of risk to the government’s IT environment has widened. Further, some have to use their own devices, and others rely on unsecured networks.
Government agencies such as the Health and Human Services Department (HHS) and the Champaign-Urbana Public Health District in Illinois have already been targeted, and it’s likely that the threats will not stop.
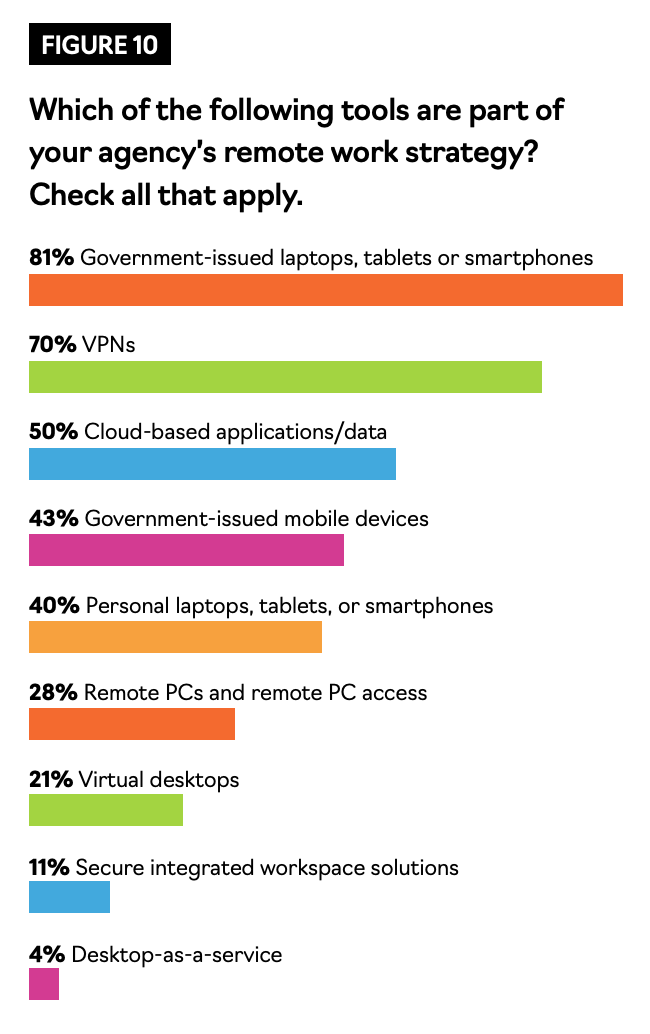 One of the most common security solutions for remote work is a virtual private network (VPN), which encrypts a device’s connection to an internal network. Seventy percent of respondents said that it is part of their agency’s remote work strategy (See Figure 10).
One of the most common security solutions for remote work is a virtual private network (VPN), which encrypts a device’s connection to an internal network. Seventy percent of respondents said that it is part of their agency’s remote work strategy (See Figure 10).
But through VPN, there are some vulnerabilities that can be taken advantage of if best practices are not applied, especially in the case of personal devices, said Steve Nguyen, Vice President of Public Sector at Citrix.
According to the survey, 40% of all respondents use personal laptops, tablets or smartphones for work (See Figure 10).
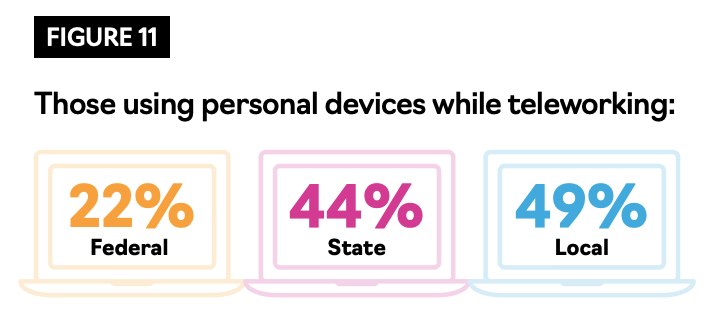
Among federal, state and local employees, state and local employees were the most likely to use these devices — 44% and 49%, respectively (See Figure 11).
While VPN secures the device’s connection, it does not secure the device. If the device itself is not secure from viruses and malware, bad actors can infiltrate the device through, for instance, a phishing email, and then jump into the VPN and have access to the whole network, Nguyen said.
“There’s been a huge spike in the amount of malicious activity, knowing that all of a sudden, there’s hundreds of thousands of people that are working from home,” Nguyen said.
In mid-March, the Cybersecurity and Infrastructure Security Agency (CISA) issued an alert for partner organizations regarding telework and VPNs.
The agency identified a few key recommendations to strengthen an organization’s VPN security during this time:
- Update VPNs, network infrastructure devices and telework devices to the latest software patches
- Alert employees to be aware of an expected increase in phishing attempts
- Ensure IT personnel are prepared to ramp up the appropriate remote access cybersecurity tasks, per National Institute of Standards and Technology (NIST) guidance
- Implement multi-factor authentication on all VPN connections
- Ensure IT security personnel test VPN limitations to prepare for mass usage and, if possible, implement modifications for users who need higher bandwidth
These measures could be boiled down to four action items: update software, alert all employees, support IT personnel and authenticate users.
This article is an excerpt from GovLoop’s recent report, “Continuity After COVID-19: Rising to the Challenge of Remote Work.” Download the full report here.





Leave a Reply
You must be logged in to post a comment.