Cybersecurity is an inescapable and urgent priority for everyone. No matter what sector you’re in or what device you’re using, securing your information and network is critical.
To help keep you in the cyber loop, GovLoop’s 4th Annual Government Innovators Virtual Summit hosted the session: Cybersecurity Trends and Strategies You Need To Know. During this session, we had the opportunity to hear from four fantastic speakers:
- Barry Condrey, Chief Information Officer for Chesterfield County, Virginia
- Diane Burley, Ph.D., Cyber Workforce Expert and Professor for Graduate School of Education and Human Development at George Washington University
- Ashley Stevenson, Identity Technology Director, ForgeRock Office of the Chief Technology Officer
- Daniel Hanttula, Director of Information Security, State of Oklahoma
Our guests covered four essential components of cybersecurity: (1) Improving the cyber workforce, (2) Building & strengthening public-private partnerships, (3) Developing an effective identity and access management strategy, and finally, (4) Preparing for what’s coming next.
Improving the Cybersecurity Workforce
Starting off the session, Condrey informed the audience that information security (infosec) is everybody’s responsibility. While some infosec program focus on strong password management or technological tools, they often forget about the most critical component: people.
This is especially important in an environment where government must do more with less. When employees are overworked and disengaged, they can make simple mistakes that present serious risks to their organizations.
After all, cyber adversaries do not only target systems, said Condrey. With spear phishing and other hacks, “YOU are the target,” he said.
Along these lines, agencies must reinforce cyber basics to their workforce. Consistent communication among various touch points – newsletters, meetings, trainings, etc. – will help make infosec part of your agency’s culture.
Education and training are also critical to fight cyber insecurity. Condrey advised that training be engaging and relatable, because no matter what tools or tech an agency has, informed employees are the best defense against cyberthreats.
Building & Strengthening Public-Private Partnerships
Similar to the previous speaker, Barley emphasized that everyone is a part of the cyber workforce. And in a broader sense, cybersecurity is a shared responsibility across all sectors. Therefore, public-private partnerships (PPPs) can go far to help in such a demanding endeavor as cybersecurity. But, what are PPPs?
“PPPs are agreements of varying forms where the public and private sectors collaborate to provide service,” Barley said. “As they relate to cyber, PPPs are increasingly popular in addressing gaps in the security lifecycle.”
To be successful, gov and industry need to have clearly defined goals, shared objectives, an articulated strategy, a clear value proposition, and very importantly, trust – especially when dealing with information sharing.
Barley also laid out key PPP implementati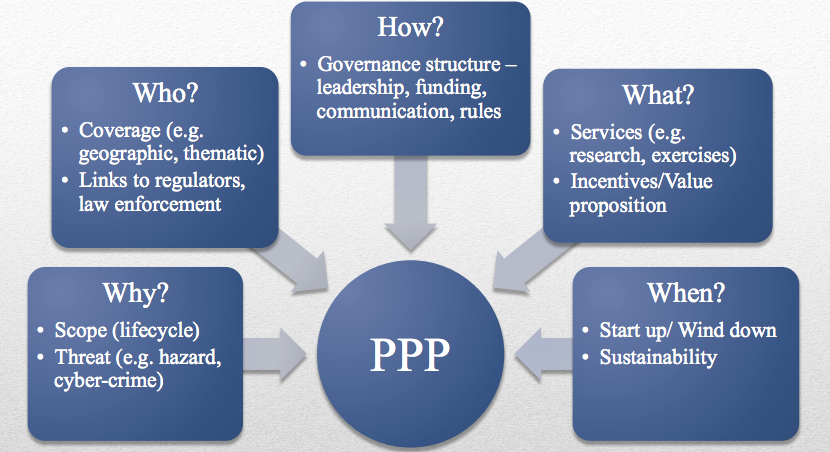
Finally, Barley provided some examples of cyber PPPs such as National Cybersecurity Center of Excellence (NCCoE) and the Critical Infrastructure Cyber Community C³ Voluntary Program.
Developing an Effective Identity and Access Management Strategy
Switching focus a little bit, Stevenson discussed why identity matters to an organization. When looking at an agency’s mission and security, he explained that there are many different users who need access to the network. Agencies need to ensure that the right people are getting access to the right things.
To ensure secure access, there is a process from digital identification, to credential, to authentication, to authorization, which finally leads to access. This is crucial, especially as tech, devices, and other things become increasingly interconnected. “Identity is the means, but secure access is the goal,” said Stevenson.
We’ve come a long way from the “castle mentality,” where the focus was on perimeter defense and keeping outsiders out of a network. Today, when information is shared and devices are connected, you can’t just put up a wall. Consequently, there is a special need for digital identities, credentials, and authentication – especially when information on a network is private and highly sensitive. And it’s not just about managing identities and putting them in a directory – it’s about securing access over the lifecycle, said Stevenson.
“Today, identity is the new perimeter,” he said. “Dynamic identity and access management is needed for any connected thing, from anywhere, on any device.”
Preparing for What’s Next
To wrap things up, Hanttula spoke about some of the exciting new cyber initiatives in the State of Oklahoma. Within the heart of OK’s Security Operations Center, Hanttula’s in-house CyberWARN system protects mission critical networks and state digital assets 24/7, 365 days a year. The system provides real-time filters to give the state centralized situational awareness.
Hanttula also explained some of the open source software the state uses, such as LAMP and ELK stack. They even have the “IPew Attack Map” which displays originating attacks and visualizes threats on a daily basis. The collaboration and continuous improvement of open source is especially helpful when cyber criminals are always advancing their methods. For example, adversaries continuously find new ways to capitalize on fear through social engineering and phishing hacks.
But just as Barley explained earlier, Hanttula also reminded us that agencies don’t need to face this task alone. US-CERT, the FBI, state information sharing and analysis centers (ISACs), as well as more informal relationships between cyber professionals can prove quite useful in securing agency networks.
While there will never be an overarching, catch-all solution to cyber, the four speakers covered essential topics regarding the people, processes, and technology that you need to stay secure.
