It’s a scary digital world out there. A recent GAO study found that cyber attacks on government have increased 782% between 2006 and 2012. With increasing amounts of sensitive data stored in your network or cloud, your agency faces risks that are not to be taken lightly. It’s not all doom and gloom, however. There are steps your agency can take to be secure and protected.
At GovLoop’s online training, Secure Your Network & Protect Your Agency, John Burger, President and Owner of Cyber Security Insights, LLC and Lee Vorthman, CTO of Federal Civilian Agencies & Cyber Initiatives at NetApp joined us to give some valuable advice on how your agency can stay secure.
To start us off, Burger provided some context to understand where your agency stands on the 5-stage cyber defense maturity model.
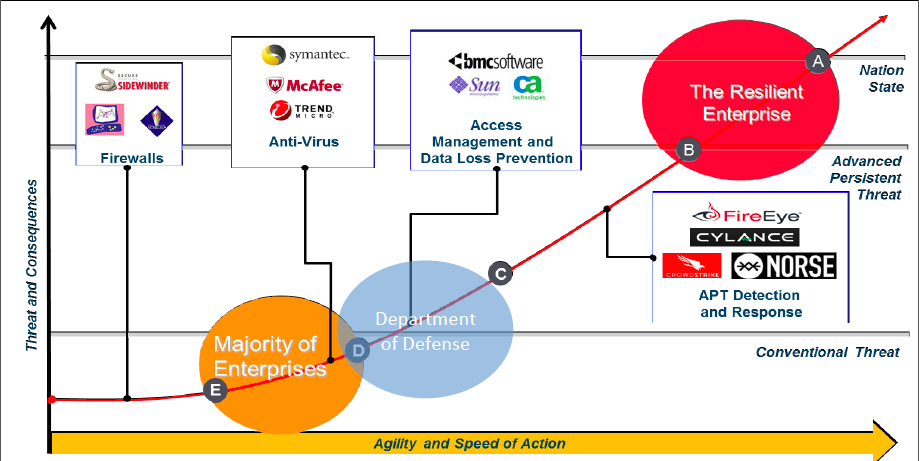
E. Reactive and Manual: The first, beginner stage where people may have Firewalls but are usually doing their best to “put out fires.”
D. Tools-based: A majority of enterprises lie within this stage and are very stove-piped, lacking integration. These organizations apply tools and technologies piecemeal to assist people in reacting faster.
C. Integrated Picture: Burger says the DoD is around this point, where defense is loosely integrated with focus on interoperability and standards-based data exchange for situational awareness.
B. Active Defense: Predictive and agile, there are operationalized incident response. Events are illuminated to help operators find, fix, and defeat the threat. Attacks will still likely have business impact, however.
A. Resilient Enterprise: The top of the line. Like active defense but matured to a point where responses can isolate and contain threats and have no impact on business or key enterprises operations. Operations can continue despite attacks.
Technology is critical to becoming a resilient enterprise, but alone is insufficient. Cyber situational awareness is key to enabling action. This is the ability to see yourself, the enemy, and the terrain, Burger explains. This awareness informs the risk formula for your agency: C + I + V + I = R. Now, solve. Just kidding.
C and I are the “capability” and “intent” of a threat that involve network events and intelligence. V and I are the “vulnerability” and “impact” of an attack on your agency. What can be exploited in your agency and how severe would the impact be on critical missions/enterprises? These factors paint an accurate picture of the risk your agency faces. Just a few years ago, this self-analysis would only be necessary once a year. With the rapid evolution of threats today, however, risk assessments must be done on a much more frequent basis.
Vorthman also emphasized the importance of factors that shape risk. He listed many, some of which included the de-perimeterization of networks where employees each have their own devices, making networks more permeable; the high degree of military and economic dependence on digital systems; and the increasing sophistication and capabilities of adversaries that are usually in lockstep, if not ahead, of cyber defenders.
With these risks in mind, NetApp’s security solutions approach involves the following three components:
Collect: Performance and density. Gather all of the data on your network. The more data you have, the better you can understand your risk.
Analyze: Flexible environments. Develop cyber intelligence that allows rapid analysis of threats in your environments. This extends your kill-chain – the series of steps an adversary must take to attack you – giving you more time to disrupt and block adversaries from reaching critical data.
Secure: Integrated data protection. Protect your data from attackers through encryption, access management, and other methods.
NetApp also focuses on the depth of defense and encourages organizations to build the following tenants into their security solutions: (1) secure protocols for data access, (2) antivirus support, (3) secure multi-tenancy, or separation of workloads (in cloud), (4) encryption, (5) file-based security, (6) industry certifications to verify security products meet industry requirements and regulations, and (7) third party partnerships to allow the integration of best practices and technologies.
So, now what? What if your agency does not have the funding, resources, or expertise to meet these standards?
Just take a look around your office, Burger offers. Sometimes government focuses too much on external actors and forgets the small things that your average employee can do. More deliberative risk planning and awareness can leverage the staff you have to improve your agency’s security significantly. Vorthman and Burger echoed the importance of a suite of tools, but don’t underestimate the impact you, yourself, can make.
For more great advice, watch the full presentation here!
