What HTTPS Everywhere Means for Federal Agencies
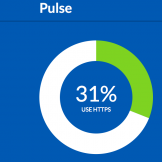
On Monday, June 8, the White House Office of Management and Budget (OMB) released a final memorandum mandating that all Federal websites implement HTTPS (Hypertext Transfer Protocol Secure). By December of 2016, all Federal websites will need to implement HTTPS for all communications. Why the Mandate? Privacy, web communications, and encryption are certainly in theRead… Read more »