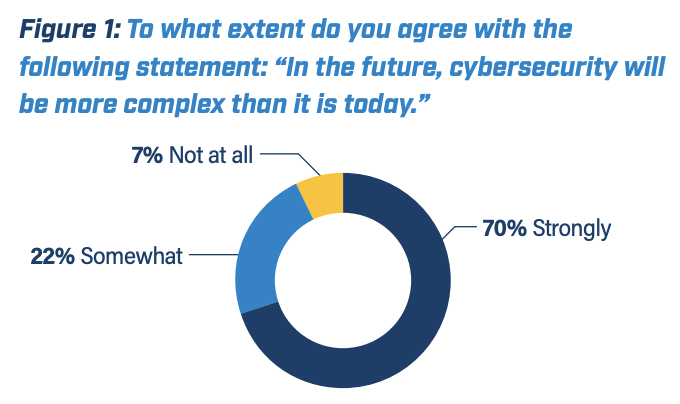
Within the government IT community, the consensus is that cybersecurity has become more challenging, a trend that is expected to continue. Respondents in GovLoop, Check Point and Swish’s survey overwhelmingly agreed, with 70% saying cybersecurity will be more complex in the future than it is today (See Figure 1).
“It’s becoming more complex due to the complexity of advanced technologies and the types of threats and attacks,” said Glen Deskin, Check Point’s Head of Engineering for the Mid-Atlantic region. “They’re becoming more complex because of multi-cloud environments, multiple risks from the internet of things, mobile devices, traditional data centers and desktops. The attack surface is increasing exponentially. Data is moving everywhere…and that makes the security challenge more complex.”
At the federal level, agencies are consolidating assets across data centers, which is producing more shared services, typically in a private on-premises cloud environment. In some instances, one entity could host many organizations in its cloud environment.
“Security really matters,” said Sean Applegate, Chief Technology Officer (CTO) at Swish. “There’s a lot more aggregation points where people are mixing different desktops and differing levels of control or security that might be using the same applications.”
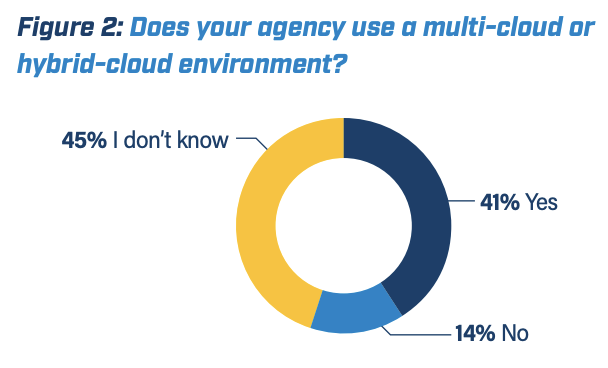
Agencies are adopting public cloud at an accelerated rate, with varieties such as Infrastructure-as-a-Service (IaaS), Platform-as-a-Service and Software-as-a-Service (SaaS) containing multiple levels of trust. Nearly three times as many respondents said their agency uses a multi-cloud or hybrid cloud environment (41%) as those that didn’t (14%) (See Figure 2).
With multiple clouds, security is more complex. During the COVID-19 pandemic, the sharp rise in teleworking has increased traffic on the internet, a low-trust environment. Organizations might have shared services in a high-trust environment on premises in a private cloud. Simultaneously, an agency might use a medium- to high-trust cloud environment through a service provider.
“The ability to control the security, whether it’s in SaaS or IaaS or an on-premises cloud, is very challenging,” Applegate said. “It’s not just setting the regulations and the policies and checking for compliance. It’s enforcing the controls in a consistent manner across those properties.”
Moving to the cloud highlights several security challenges:
Data breaches
Security measures used to protect on-premises networks don’t work as well in the cloud, if at all. Inspecting all traffic entering and leaving clouds can prevent breaches that otherwise could spread to other off-premises assets.
Compromised accounts
To get at cloud assets and data, hackers use many tools, including scripting, keylogging, spear phishing, brute force attacks and exploitation of weak passwords.
Insider threats
To adequately protect data in the cloud, security solutions must account for the behavior of potential insider threats, both purposeful and unintentional.
Poorly secured APIs
Application programming interfaces (APIs) are used to customize cloud services. When compromised, they can be used to manipulate cloud environments.
Encryption
Inadequate encryption of data in the cloud can compromise the integrity of critical information, a problem that grows as more workers use personal devices.
Agencies need a way to consolidate and consistently deploy security policies into a central business-centric engine. It should be readily applied at the right technical level across multiple environments and applications in public, private and hybrid clouds.
This article is an excerpt from GovLoop’s recent report, “Adaptive Security in a Complex Cloud Environment.” Download the full report here.
