By Karen D. Schwartz
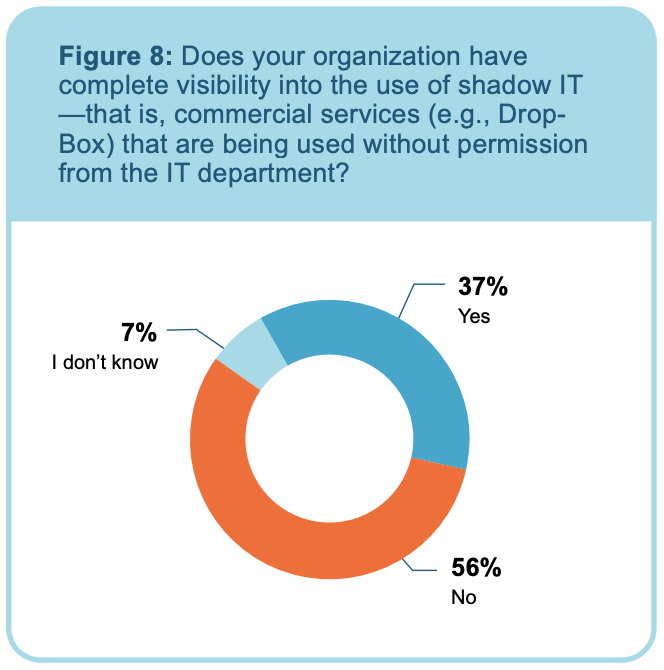
There may not be a large organization in existence that hasn’t experienced the repercussions of shadow IT. Shadow IT — that is, hardware, software and services being used by employees without the approval of the IT department — can be a serious problem. Despite the dangers, more than half of respondents to the survey said their organizations don’t have complete visibility into the use of shadow IT (see Figure 8).
One recent report found that 97% of cloud apps used by enterprises aren’t managed by a centralized IT or security function. Instead, they were brought on and used by individuals within the organization, without approval. The same report also found 83% of users routinely used personal apps on managed devices.
“Whatever tools you use, make sure you can achieve very granular visibility into the use of shadow IT. It’s also important to have comprehensive data loss prevention (DLP) coverage — and the more advanced the DLP capabilities, the better.” – Matt Clark, Netskope senior cloud security engineer
Since it’s difficult to determine when a shadow IT service may be involved, agencies should always encrypt sensitive data, which protects the data if it falls into the wrong hands, and decrypt the traffic to understand the types of data flows that are occurring.
Other critical capabilities include:
- Supporting real-time malware inspection on traffic entering and exiting cloud services
- Applying and enforcing adaptive policies based on content and context
- Layering policies with “allow” and “block” actions
- Discerning the difference between sanctioned versus unsanctioned (i.e., shadow IT) instances of the same application
Left unchecked, shadow IT can result in:
Loss of visibility and control, resulting in security vulnerabilities
The IT department can’t monitor and control what it can’t see. That means that software, hardware and other shadow IT may contain vulnerabilities that can’t be addressed because they aren’t known or identified. For example, if an employee emails data from a shadow IT application to someone outside the agency, that data immediately becomes public. Similarly, if an employee uses his or her own private instance of Microsoft 365 instead of the sanctioned version, data may inadvertently be shared between the two, introducing security vulnerabilities.
Noncompliance
Public sector organizations must comply with a host of standards and regulations, and go to great lengths to ensure that systems, software and other technologies meet those standards. It’s relatively easy for shadow IT to evade detection and cause the entire agency to become noncompliant if the IT department lacks visibility and granular policy controls.
Additional Cost
There are many potential expenses associated with shadow IT, including noncompliance fines, security remediation costs and operational costs due to underutilization of sanctioned applications.
Data Loss
Data accessed or processed by unapproved software is more likely to be compromised or lost. Because shadow IT isn’t connected to an agency’s backup or storage systems, any outage is likely to result in permanently lost data. Data can also be permanently lost when an employee leaves the agency, but has been using personal accounts to store agency data.
Visibility is the key to preventing and managing shadow IT. That means implementing the right tools like CASB to discover cloud services and other shadow IT technologies.
This article is an excerpt from GovLoop’s research brief, “Putting Security Front and Center in the New World of Hybrid Work.” Download the full report here.





Leave a Reply
You must be logged in to post a comment.