Government networks are faced with millions of cyberthreats each day. Responding proactively to these security events is a top priority across federal, state and local governments.
GovLoop hosted an online training titled “Redefining Security- Govs Embrace Cyber Framework” that addressed how governments are enhancing cyber efforts through the adoption of the National Institute of Standards and Technology’s (NIST’s) Cybersecurity Framework (CSF).
What exactly does the CSF recommend and how can governments use it to tackle their own unique organizational concerns?
Ken Durbin, Sr. Strategist of Global Government Affairs and Cyber Security, Symantec, and Matt Barrett, NIST Program Manager, Cybersecurity Framework, spoke at the training.
First, Durbin pointed out that the CSF is celebrating its five-year anniversary, and over half a million downloads. “By 2020, a Gartner survey predicts that 50 percent of organizations will have adopted the NIST framework,” he said.
The CSF is used in a wide range of countries. “Soon, an estimated two billion people will be able to read the framework in their own language,” Barrett explained.
So what exactly are the five key functions of the CSF? They include:
- Identify– Organizations must develop an understanding to manage cybersecurity risk to all the moving parts they have to manage, including systems, assets, data and capabilities. “A lot of foundational securities are located in this function,” Barrett said. Some sample identify activities include identifying business procedures, observing and noting information flows, putting cybersecurity policies in place that include roles and responsibilities, maintaining hardware and software inventories, driving contracts with external partners, and identifying processes to improve risk management.
- Protect– There must be a focus related to developing and implementing organization-specific safeguards to ensure secure delivery of services. “There’s something about this that’s proactive,” Barrett said. “What are we doing to prevent bad stuff from happening to our cyber?” Sample protect activities include managing access to assets and information, conducting regular backups, protecting sensitive data, patching operating systems and applications, creating plans to deal with response and recovery, and training employees.
- Detect– Agencies must implement appropriate procedures to quickly and accurately identify the occurrence of a cybersecurity event. “Detect is right in the middle of the proactive/reactive spectrum,” Barrett explained. Some procedures include installing and updating anti-virus and other malware detection software, knowing expected data flows, and maintaining and monitoring logs.
- Respond– When a cybersecurity event is detected, agencies must move quickly to take action. Some respond activities to consider include coordinating with internal and external stakeholders and ensuring that response plans are updated and tested beforehand. “When something bad is happening, it’s often important to not go radio silent,” Barrett said. “Communication is a critical part.”
- Recover– After a cybersecurity event, it is important for agencies to regroup and repair impaired capabilities or services. “How do we get back to the original services that our organization was providing?” Barrett asked. There are similarities between respond and recover, although recover is more retrospective. Sample recover activities include managing public relations and company reputation, communicating with internal and external stakeholders even more, ensuring that recovery plans are updated based on the event, and considering cyber insurance.
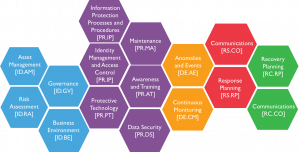
 “When you put all the categories together, you see the patchwork that happens,” Barrett pointed out. “You also see dependencies.” Here are the activities that correspond in color to each key function of the CSF:
“When you put all the categories together, you see the patchwork that happens,” Barrett pointed out. “You also see dependencies.” Here are the activities that correspond in color to each key function of the CSF:
How exactly is the framework used in organizations? “There is a typical order in which the five parts of the functions are used,” Barrett stated. The five functions are considered when communicating strategies, plans, and policies. Each implementation tier is customized and assessed to determine the current state of the agency and determine where improvements must be made. “A profile is a customization of the cybersecurity framework categories and subcategories in a way that prioritizes desired outcomes,” Barrett said. Profiles are also usually developed and implemented to manage requirements and ensure that agency priorities align with a set output.
NIST provides resources to help the implementation of the CSF. Success stories of CSF use include the University of Chicago, the Japanese Cross-Sector Forum, and the University of Pittsburgh, among others.
However, there are a few implementation challenges agencies might face when aligning procedures to the CSF. First, governmental organizations are federated, meaning there are multiple layers and they often operate individually of each other. Creating a comprehensive view of cybersecurity requires coordination across multiple departments, agencies, divisions, and institutions. “Organizational structures of government can be a challenge,” Durbin said. “You want to think about that during your planning.”
There are also naturally multiple compliance requirements, a lack of key stakeholder buy-in, budgetary constraints, and a “one and done” mentality.
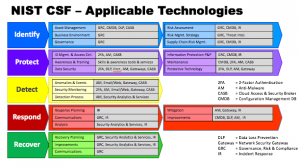
A number of applicable technologies apply to the five aspects of the CSF:
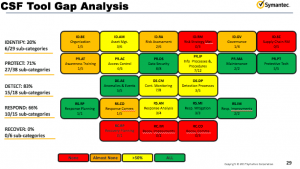
There are a number of tool gaps, however:
How are you implementing the CSF in your agency? Let us know in the comments below.
Photo Credit: NIST





It’s great how you organized this post – first making a list of the five key functions and their descriptions, and then including helpful images for readers to thoroughly understand NIST’s CSF. Also interesting to note that CSF is so successful in Japan!